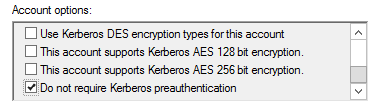
Due to an old legacy option ('Do not require Kerberos preauthentication') in Kerberos, it is possible to request hashes of all users that have this option ticked in the account options.

Prior to Kerberos version 5, Kerberos would allow authentication without a password. In Version 5, it does require a password, which is called Pre-Authentication.
When a client performs AS-REQ (Authentication Server Request) normally it encrypts the request with a password and a timestamp. The KDC (=DC) then reads the request and decrypts the request using the user password which is stored on the DC.
When a preauthentication is not required, the request is not encrypted with a password (As no password is needed to authenticate, due to this legacy option). Therefore an attacker can send a fake AS-REQ which the KDC will grant a TGT ticket to, as there is no password needed for verification.
Accounts with the flag 'DONT_REQ_PREAUTH' explicitly set for them can be found, and their hashes pulled.
| Flag | Value in hexadecimal | Value in decimal |
|---|---|---|
| DONT_REQ_PREAUTH | 0x400000 | 4194304 |
Password hashes can be pulled from that request and cracked offline, but then a successful attack is still reliant on weak password complexity.
Note: When accessing systems with any Kerberos attack, use the netbios or full host name, NOT the IP address!
'Rubeus' can be used to find accounts which have 'DONT_REQ_PREAUTH' set by running
.\\Rubeus.exe asreproast
If no other arguments are supplied, all applicable user accounts are roasted.
Other argument that can be included: